
By Tony D’Ambrisi, Senior Product Director, Deltek
Katie Arrington, Chief Information Security Officer, Acquisition and Sustainment at United States Department of Defense, has said that as a nation we are losing $600 billion annually to intellectual property theft and with some information technology (IT) security basics, a government firm could reduce that number. According to the Department of Defense (DoD), there are nearly 221,000 unique contractors and subcontractors in its supply chain which adversaries see as opportunities to exploit; organizations who hold valuable data, with several having a wide variety of cyber defensive strategies and practices. Threat actors look to maximize their return on investment while reducing risk to themselves and their sponsors by focusing efforts on organizations that have weaknesses in their cyber defenses and practices. These cyber criminals are betting that not all 221,000 DoD prime contractors and subcontractors are maintaining proper cyber defenses, which creates opportunities to harvest and exploit valuable data for financial gain, and at the same time, putting the country at risk.
In October 2020, the National Security Agency (NSA) issued a bulletin that warned of Chinese sponsored threat actors exploiting 25 specific common vulnerabilities and exposures (CVEs) to exploit computer networks holding intellectual, military, economic and political information. The targets included the U.S Defense Industrial Base and its supply chain organizations. The NSA recommended organizations prioritize their patching and mitigation efforts to prevent entry and persistent presence in targeted networks. A threat actor establishing an undetected presence could lead to additional nefarious activity, such as exfiltration of intellectual property or an interruption of business operations, commonly seen as part of a ransomware attack.
Defending against nation state-sponsored activity certainly seems like a tall order for most organizations. “Keep your patching activities a priority and current,” is well known advice, but practitioners know it is a complex challenge which is why opportunities exist for bad actors. So, where would one start with such a challenging task? How can you know which are the highest risk vulnerabilities to your organization that should be prioritized and acted on?
The path to effective patching and remediation starts with a solid organizational foundation. Let’s begin by looking at two foundational questions all organizations should be asking themselves:
Who is your CISO and who does she/he report to?
Several reports state that a governance led CIO/CISO supported organizational structure can set the foundation for success. It is key that the CIO/CISO report directly to senior executive leadership and have the authority and oversight to direct changes across the entire organization.
How many hats are your cyber defense team members wearing?
When leadership and front line defenders wear multiple hats, inconsistent communication and execution of tasks can occur, rendering well-intentioned efforts useless or ineffective. Playing multiple roles at any level can create weaknesses throughout an organization’s cyber defensive process and procedures.
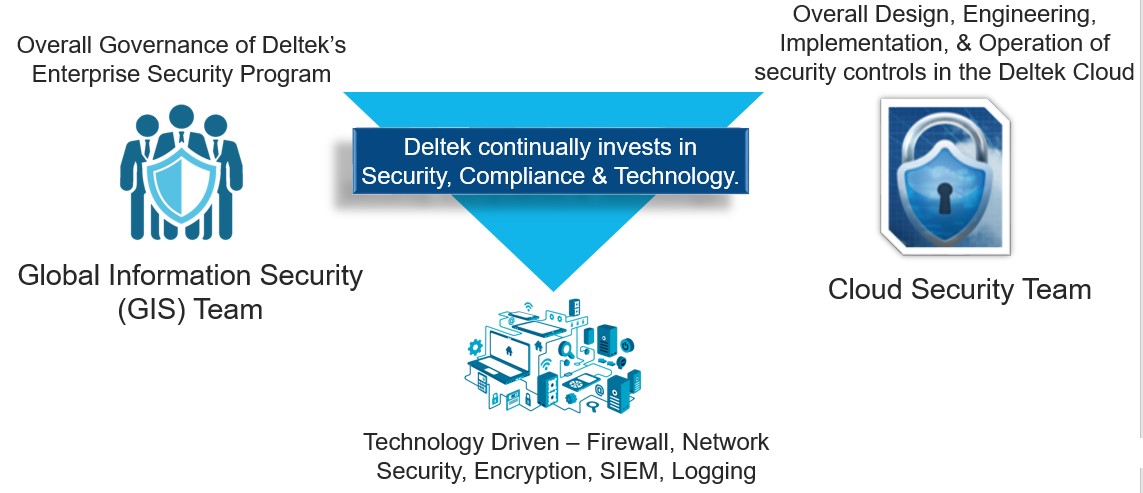
Deltek’s Investments Improve Your Cyber Posture
Not all organizations have the luxury of depth and breadth in staffing their cyber defense teams. Each year, Deltek increases its investment in security, compliance and supporting technologies for our Deltek Costpoint cloud customers. The recent release of GovCon Cloud Moderate is simply a current example of how Deltek continues to make investments to help customers working to achieve and maintain compliance. This new offering provides the Costpoint you know and love in a FedRAMP Moderate equivalent controls environment, supported by Deltek team members located in the United States.
Our Costpoint cloud and GovCon Cloud Moderate customers immediately and directly benefit from these investments from the day they are on-boarded and throughout their entire time as a Costpoint customer. Deltek has built multiple teams, with separation of duties, to ensure we are providing secure enterprise resource planning (ERP) services to Costpoint cloud customers.
As part of this continued evolution, the Deltek Global Information Security (GIS) team was created, led by Deltek’s new CISO, singularly focused on the overall governance of our Enterprise Security Program. This change was implemented to avoid multi-hatting and ensures that the mission of securing both organizational and customer data could not be diluted by organizational structure. The division of duties allowed GIS to have a central focus of staying current with the constantly evolving security and compliance requirements impacting our customers, security incident response, annual employee security training, and managing third-party assessments for our Costpoint cloud services. Deltek’s GIS team works closely with Deltek’s Engineering and Cloud teams to fully understand the risk a vulnerability presents to the services we operate. The GIS team continually evaluates the risk levels based on the presence of any system vulnerability and helps determine the priority order for addressing the risk typically by remediation activities like applying system patches.
The primary mission of Deltek’s Global Cloud Security Team is the security for our Cloud service and products. This includes architecting and implementing our Cloud solutions in accordance with the industry’s and Deltek’s compliance standards. Additionally, our Cloud experts provide real-time situational awareness into the security posture of the service, evaluate and apply software security patches and fixes, and maintain security and compliance-related documentation. For example, with the NSA bulletin mentioned previously, Deltek’s Global Cloud Security Team reviewed the CVEs to determine which ones were applicable, then tested and applied any necessary patches. Additionally, the team ensured updates were reported to the appropriate stakeholders in the organization regarding the status of risks as well as the successful remediation of the threats.
If you are finding it challenging to keep your ERP system patched and current, you should be evaluating Deltek’s Costpoint cloud offerings, including GovCon Cloud Moderate, as vulnerability management performed by Deltek personnel. Deltek is committed to delivering a secure solution, freeing your teams up to focus on other strategic tasks and efforts.

Deltek Project Nation Newsletter
Subscribe to receive the latest news and best practices across a range of relevant topics and industries.

